Cluvio is a software-as-a-service platform for data analytics. This document outlines the security architecture of Cluvio as well as topics related to the security of database connections and your data.
The Cluvio platform is deployed and runs in 2 separate locations on Amazon Web Services in the eu-central-1 (Frankfurt, Germany) and us-west-2 (Oregon, US) AWS regions. Cluvio utilizes 3rd party services, such as Recurly (billing), Braintree (credit card processing), Elev.io (in-app help), Sendgrid (email), PagerDuty (alerting) or Sentry, Pingdom and NewRelic (monitoring).
Cluvio leverages a set of best-practices that guarantee system security and data privacy:
Our infrastructure architecture successfully passed the AWS Foundational Technical Review and CIS AWS Foundations Benchmark v3.0.0.
Here is a basic overview of the Cluvio architecture, showing its role as a mediator for data access and visualisation. 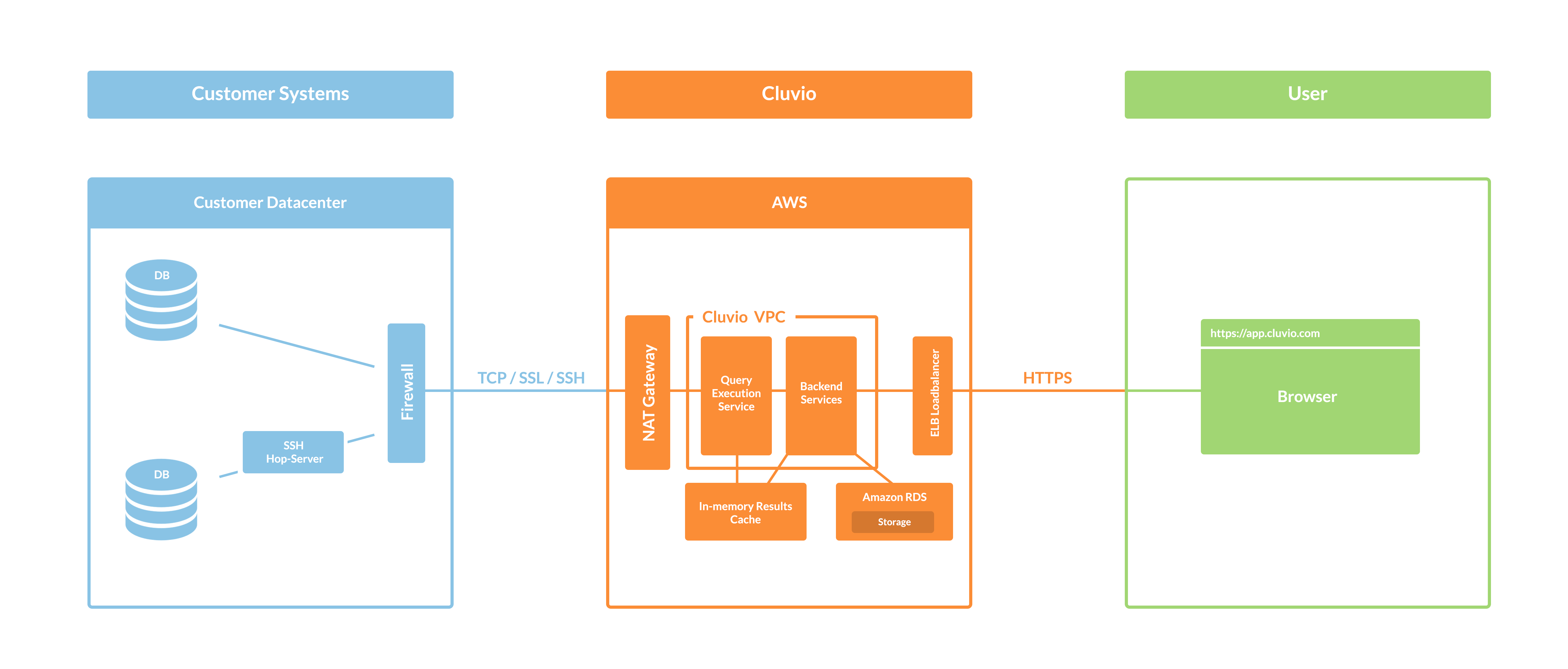
To be able to run queries that power the analytical reports, Cluvio needs read-access to your database or data warehouse. To access the data securely, Cluvio supports many approaches that evolved over the years of increasing use and acceptance of Cloud BI tools. These approaches cover both connections to cloud hosted databases like AWS RDS, Redshift, Snowflake, BigQuery or Microsoft Azure, as well as connections to databases installed on your own servers on cloud providers or dedicated hardware behind a firewall. Concretely, data access with Cluvio can be secured as follows:
More details can be found in the Cluvio Documentation.
Cluvio analytics are based on SQL and as such do not perform other operations on the database than running specific SQL queries for retrieving database metadata and running SQL queries on request of an authenticated and authorized user in order to to fetch the data that underlies the analytical reports.
The results of the database schema queries are stored as metadata as long as the originating data source exists. The results of the report query executions are stored in a transient cache within a secured Cluvio private network for up to 24 hours, after which all the data are automatically purged and no copies of it are retained.
In more detail, the queries that Cluvio performs against your database are as follows:
Any data that is either related to your account or a result of one of the analytical queries is protected in transit and at rest.
In transit security refers to security of the data as it is transmitted between the Cluvio services and the end user’s computer. All Cluvio communication is performed with transport-layer security (TLS/HTTPS). The Cluvio API is not accessible via unencrypted HTTP connections and clients requesting such connections are immediately redirected to secure transport protocols. Furthermore, all API operations that contain account information or data require user authentication and authorisation.
Cluvio stores all account data in a database that is encrypted at rest and all backups of the data are encrypted as well. User passwords are stored as salted, cryptographic hashes to prevent recovery and abuse even in the case of a compromised database. Database connection passwords or authorization strings are stored with 256-bit symmetric encryption.
All Cluvio APIs that provide access to the account data require authentication via email and password. The result of successful authentication is a time-constrained session and an access token that authorizes API access in the context of that session. The following measures are taken to prevent abuse and facilitate recovery:
Cluvio audits all changes made by a user in the context of an organization. This includes logging in or out (with IP address), running queries and creating, changing or deleting reports, dashboards or any other objects. The audit logs can be provided to account admins on request.
Cluvio employs a wide range of monitoring services that guarantee the uptime of the Cluvio platform and allow us to respond quickly to any operational problems. This includes:
The summary of the Cluvio platform status, as well as historical incidents, can be viewed at any time at http://status.cluvio.com.
Cluvio never stores results of your analytical queries other than in the context of transient caching of results (kept for up to 24 hours and purged afterwards). Account data are stored as part of a database backup in encrypted form. These backups are kept for a limited time (usually at most 30 days).
All physical storage devices of Cluvio are on AWS. Amazon AWS employs the Guidelines for Media Sanitization (NIST 800-88 or DoD 5220.22-M) where all physical devices are destroyed within Amazon premises without leaving these locations. A detailed description can be found in the AWS Security Whitepaper on page 8, section “Storage Device Decommissioning”.
Cluvio successfully completed a AWS Foundational Technical Review that is regularly re-evaluated. Cluvio continuously tracks the CIS Benchmark for Amazon Web Services as well as the AWS Foundational Security Best Practices standard.
Amazon Web Services itself complies with some of the most demanding certifications, namely:
For an up-to-date list of certifications and compliance audit reports, please see https://aws.amazon.com/compliance.
If you are a security expert or researcher and you believe that you have found a security issue in Cluvio, we encourage you to notify us at security@cluvio.com. Please make a good faith effort to protect our users' privacy and data. We look forward to working with you to resolve the issue as soon as possible and will award bug bounties if applicable.